Dear Customer,
As a customer with one or more dedicated KS servers, during installation, you have the possibility to deploy the Real Time Monitoring (RTM) component developed by our teams to monitor your machines.
A security researcher has identified a minor vulnerability on the old version of the RTMv1 monitoring tool, which can be deployed on KS Linux dedicated servers.
This vulnerability allows an non-privileged user (without access to the "root" user), but already having access to the server, to arbitrarily overwrite any file in the system, via a character string generated by RTMv1.
To our knowledge, this flaw has not yet been exploited. In addition, it is not possible for an attacker to retrieve any data.
A new version of the RTM component (RTMv2), not affected by this vulnerability, has been deployed for new Linux server installations since January 28, 2019 in Europe and since April 10, 2019 throughout all our other data centers.
Some of your services still use the old version of this component:
………………..
We strongly recommend that you upgrade to RTMv2 to protect your services. If necessary, a guide is available at the following link.
The KS Security Team
黑龙江网友:看了下,意思是必须有用户权限(包括非root用户)登录到系统,才能利用这个漏洞?
未经允许不得转载:美国VPS_搬瓦工CN2 GIA VPS » Dear Customer,
 美国VPS_搬瓦工CN2 GIA VPS
美国VPS_搬瓦工CN2 GIA VPS
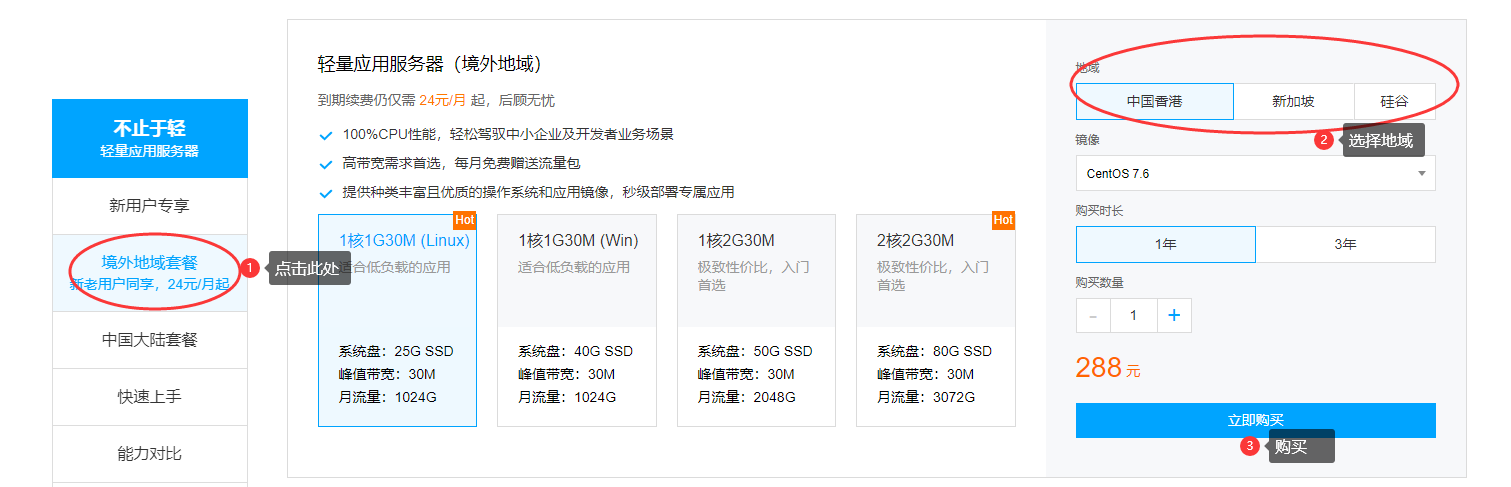 腾讯云轻量怎么购买,云轻量香港/美国/新加坡购买教程
腾讯云轻量怎么购买,云轻量香港/美国/新加坡购买教程 亏了,刚才退款了一个greencloud日本
亏了,刚才退款了一个greencloud日本
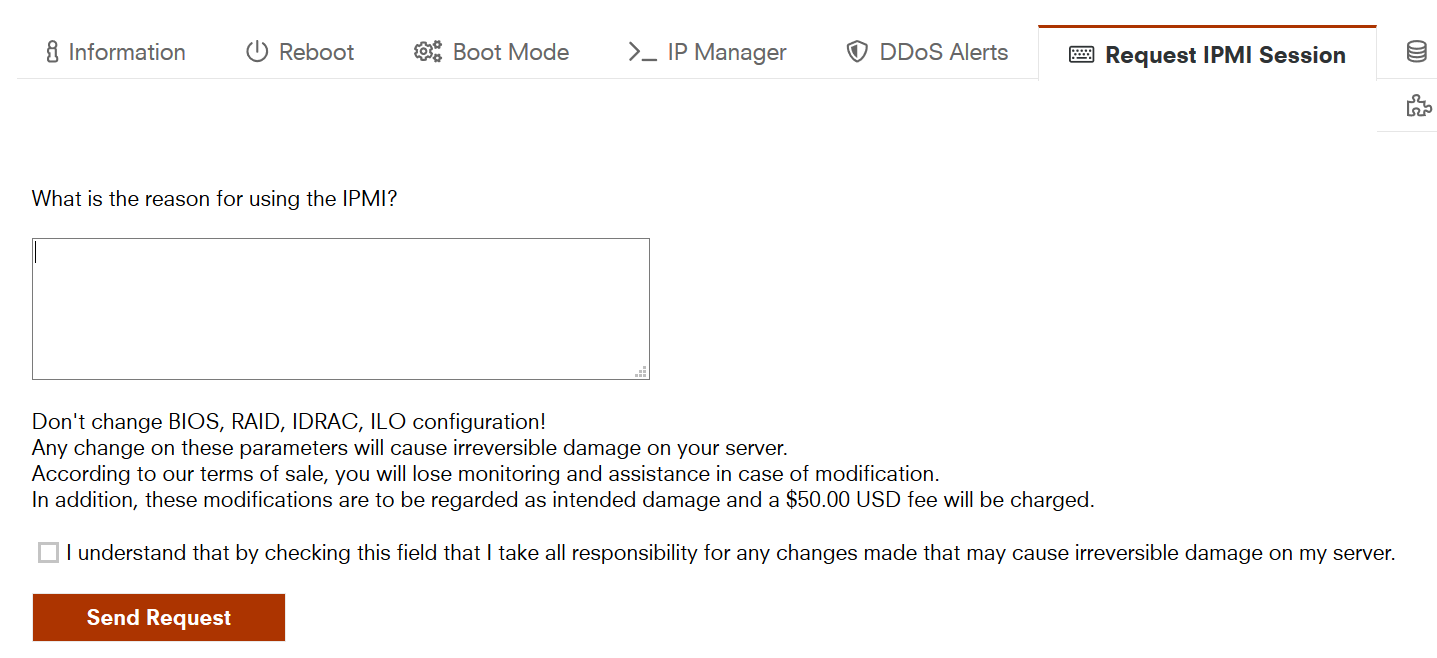 10欧的IPMI写什么申请理由好?
10欧的IPMI写什么申请理由好?